HTTP traffic monitoring can show why code that looks correct still fails on the wire: a
missing Authorization header, a redirect that drops a cookie, or a TLS handshake that never
finishes.
With HTTP Debugger Pro you can monitor HTTPS traffic, record HTTP traffic as reproducible evidence, and analyze captures fast enough to pinpoint the failing request.
What is HTTP traffic?
HTTP traffic is the sequence of client requests and server responses (also called transactions) exchanged over HTTP or HTTPS, including method, URL, headers, status codes, and bodies. Monitoring it reveals the exact bytes on the wire, which is essential when what you intended to send differs from what the server actually received.
When HTTP traffic monitoring is the fastest way to debug
An HTTP traffic monitor is most useful when behavior differs between environments or tools. Typical cases include:
- Requests that succeed in Postman or a browser but fail in your app.
- Authentication flows that break after a redirect or cookie update.
- CORS or cache issues where headers are missing or overwritten.
- Intermittent errors are tied to load balancers, gateways, or proxies.
- Performance regressions caused by unexpectedly large responses.
How to monitor HTTPS traffic (step-by-step)
The workflow to monitor HTTPS traffic is consistent across tools. The details differ, but the order matters.
- Start capture before reproducing the issue, so you include redirects, cookies, and the TLS handshake.
- Enable HTTPS decryption by installing the tool's trusted root certificate or by using a browser SSL key log file.
- Reproduce the issue once to keep the capture small and easy to filter.
- Filter by host, URL, status code, or process name to isolate the failing call.
- Compare the failing request to a known-good request and look for differences in headers, bodies, or redirects.
- Export or save the session to record HTTP traffic for teammates, and scrub secrets before sharing.
Note: If the problem occurs on your client's computer and does not recur on yours, you can ask your client to run a special, free version of HTTP Debugger Pro, which will allow them to log the problem and send you the logs for analysis.
HTTP traffic analyzer options (and when to use each)
Choose the capture layer based on what you need to observe. A browser-only issue does not require the same tooling as a desktop app or a service that runs before your debugger starts.
| Analyzer type | Best for | Strengths | Limitations |
|---|---|---|---|
| Browser DevTools | Front-end API calls and page loads | Zero setup, timing breakdowns | Cannot see other processes or background services |
| Proxy-based debuggers | Apps that can be pointed to a proxy | Full request/response visibility and replay | Requires proxy config and HTTPS interception |
| Proxy-less system capture | Multiple processes or apps started before capture | Sees traffic without changing proxy settings | Often Windows-focused implementations |
| Packet capture (pcap) | Low-level network diagnostics | Protocol-level detail and timing | Encrypted payloads without decryption keys |
What to inspect in HTTP traffic
Request line and headers
Verify method, URL, and critical headers such as Authorization, Content-Type, Accept,
and User-Agent. Small header differences often explain 401, 403, or 415 responses.
Response status and headers
Look for cache headers, redirects, and auth challenges. A 200 with a Set-Cookie header missing an
expected Path or Domain attribute can scope the cookie differently than intended and
break a session in production.
Timing and size
Compare server time to payload size. A fast 500 can indicate immediate validation failure; a slow 500 can point to upstream timeouts or dependency issues.
A practical analysis workflow (real example)
Example: an API returns 415 Unsupported Media Type only in production. The capture shows the client is sending form data while the server expects JSON.
POST /v1/orders HTTP/1.1 Host: api.example.com Content-Type: application/x-www-form-urlencoded
Changing the request body to JSON and setting Content-Type: application/json resolves the issue.
This is the kind of mismatch an HTTP traffic analyzer exposes immediately.
Common pitfalls when you monitor HTTPS traffic
- Capturing too late. If you start after reproducing the bug, you miss the initial redirects or cookies that caused it.
- Seeing only CONNECT tunnels. If HTTPS decryption is not enabled, you will see encrypted payloads instead of headers and bodies.
- Missing localhost calls. Proxy-based tools may bypass
localhosttraffic; use system-wide capture or target the machine name instead. - Confusing HTTP/2 multiplexing. Multiple requests share one connection, so ordering must be read per stream, not per socket.
- Sharing secrets. Captures often include tokens or cookies; sanitize them before sending logs to support.
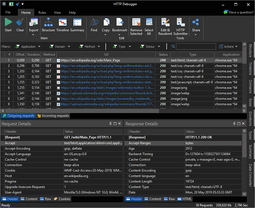
Using HTTP Debugger Pro to record HTTP traffic on Windows
If you need system-wide capture without proxy configuration, HTTP Debugger Pro is a proxy-less HTTP traffic monitor for Windows. It captures traffic at the network driver level without changing system proxy settings, so it can see traffic from apps started before the tool launches. It can decrypt HTTPS traffic from browsers, .NET apps, Java apps, and Android emulators without installing server certificates.
For analysis, it offers process-based filtering, advanced filtering rules, built-in viewers for headers, HTML/JS/CSS, XML/JSON trees, cookies, URL parameters, and images, plus traffic visualization charts for slow or large requests. You can edit and resubmit requests, use the auto-responder, or apply the HTTP Modifier to change headers or content on the fly. Sessions can be saved and restored, and exports include Excel, XML, JSON, CSV, TXT, or binary formats.
FAQ
-
How do I monitor HTTPS traffic?
Start capture before reproducing the issue, enable HTTPS decryption, then filter by host or process. This is the fastest way to monitor HTTPS traffic without losing the initial redirects or cookies.
-
Do I need to install a certificate to monitor HTTPS traffic?
Yes for most tools. HTTPS is encrypted, so you must install a trusted root certificate or use a browser SSL key log file to see headers and bodies.
-
Can a proxy-based tool capture localhost traffic?
Often no. Many frameworks bypass proxies for
localhost. Use a system-wide capture method or target the machine name or local IP instead oflocalhost.